BGP Hijacking - What is it and how to prevent it?
Table of Contents
BGP stands for Border Gateway Protocol, more commonly known as the system that keeps the internet (and by definition, routing) working correctly. Sometimes misconfigurations (Like accidentally announcing a wrong prefix) can break the internet. In this blog post, I will explain BGP Hijacking and how to prevent it. Primarily for people without network experience.
BGP Hijacking #
BGP Hijacking is when an internet provider announces a subnet of IP addresses when that provider doesn’t have the authorization to do so. This happened recently when ProtonMail’s IP addresses got announced by Telstra.
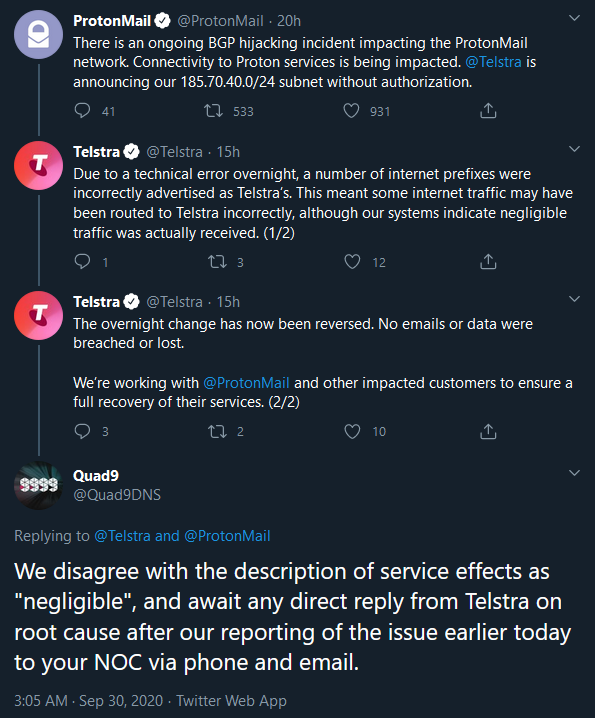
It could happen by accident (misconfigurations) or by someone with malicious intent. By announcing someone’s subnet you get traffic to your network instead of the network it should normally go to. If you would do this with malicious intent you can use this to pretend to be the service and steal the users data. This has happened before when a BGP Hijack on Amazon’s DNS services got the cryptocurrency wallets of MyEtherWallet users stolen.
Luckily, there is a way to prevent this…
Preventing BGP Hijacks - RPKI Filtering #
RPKI stands for Resource Public Key Infrastructure. This system uses public keys to authenticate if you are allowed to announce the subnet and with filtering your internet provider can reject the range if it is invalid. This way the subnet won’t get propagated. Unfortunately, not all Internet providers have implemented this yet.
If you work at an ISP and have no idea how to implement RPKI, be sure to take a look at this site! It could help you to start implementing this in your organisation. https://rpki.readthedocs.io/en/latest/about/faq.html
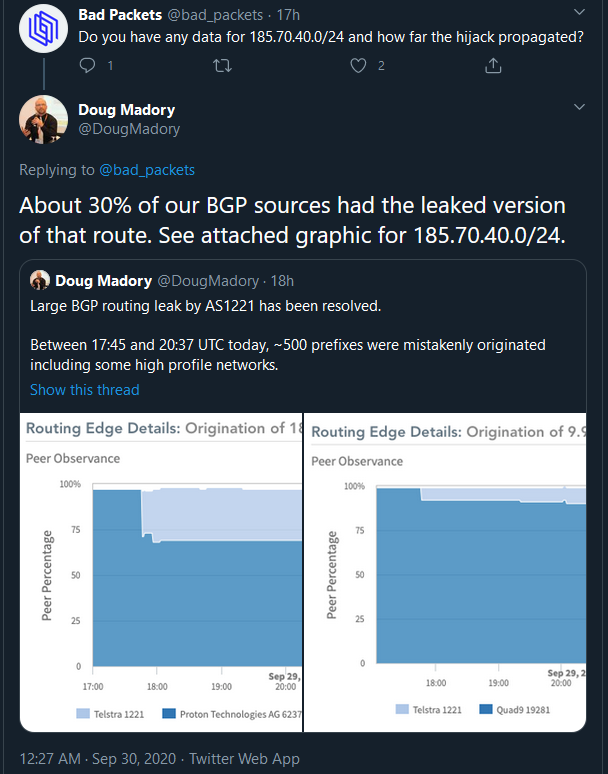
If all Internet Providers had implemented RPKI Filtering, there wouldn’t have been a routing issue because of the misconfiguration. The one’s that did were unaffected by the invalid announcement. As for example can be seen here, the providers that implemented proper filtering were unaffected.
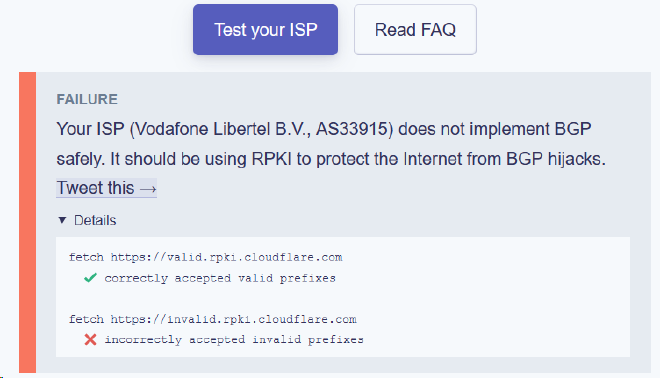
If you want to check if your own internet provider implements RPKI yet, go to Cloudflare’s https://isbgpsafeyet.com/ website and press the “Test your ISP”. For example, my provider Vodafone / Ziggo (AS33915) doesn’t support RPKI filtering yet. Be sure to let your provider know how important this is and ask them when they plan to implement this.
As always, feedback on these posts are welcome via the contact form or other ways to contact me in the sidebar.